It was more that one and a half years ago when I proposed creating a new security &QA focused port for Debian and now I’m happy to share the first bits of it.
Last year I started the bootstrapping during the holidays and I now have the prototype in the form of cross built packages which can be installed next to amd64 packages using multiarch.
The aim of creating the port is still the same, letting people mix fast (amd64) and reasonably hardened (hardened1-linux-amd64) packages on the same system. (Only for QA purposes for now, see update 3.)
You can already try the cross-built packages in an amd64 unstable chroot, but be warned that the packages are not stable yet.
In the following session I tested curl which seems to be working OK, and groff, which seems to be too buggy even for debugging:
debootstrap --arch=amd64 unstable test-hardened1
# mount /proc for ASAN
mount --bind /proc test-hardened1/proc
chroot test-hardened1/
apt-get install debian-keyring
# this is my key, I'll create one dedicated release key later
gpg --keyring /usr/share/keyrings/debian-keyring.gpg -a --export 0x21E764DF | apt-key add -
echo "deb http://hardened1-debian.s3.amazonaws.com/debian-cross-built hardened1-unstable main" >> \
/etc/apt/sources.list
apt-get update
# update apt and dpkg to versions handling the new port
apt-get upgrade
apt-get update
dpkg --add-architecture hardened1-linux-amd64
apt-get update
apt-get install curl:hardened1-linux-amd64
curl -s https://www.debian.org | tail -n2
</body>
</html>
apt-get install -t hardened1-unstable groff:hardened1-linux-amd64
groff
ASAN:SIGSEGV
=================================================================
==20642==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000000 (pc 0x7f79cd84698a bp 0x619000006980 sp 0x7ffe89b3a930 T0)
ASAN:SIGSEGV
==20642==AddressSanitizer: while reporting a bug found another one. Ignoring.
The next steps are finalizing the changes to apt, dpkg, GCC, glibc and other packages, rebuilding all packages in hardened1-linux-amd64 sbuild chroots and building the rest of the archive.
Some of the patches are not submitted yet but they are available in a temporary fork of rebootstrap
I hope I’ll be back soon with the recompiled and finalized packages, but until then feel free to try the cross-compiled ones! Patches fixing crashes are always welcome! 🙂
update 1: Some packages like dpkg-dev are not installable, I’m working on them.
update 2: There is one similar project I know of which aims creating an address sanitized Gentoo variant and Hanno Böck will give a presentation about that at FOSDEM.
update 3: Note that using ASAN in its current form opens new attack surfaces thus it is not recommended for securing systems especially since it is incompatible with kernels with Grsecurity patches. The port is in current form allows detecting a lot of bugs thanks to ASAN, but as mentioned int thread at oss-security, but don’t use it on production machines. Experiments with the port might pave the way for an Address Sanitizer version which could be for improving system’s security without opening new ways of bypassing protection.
 Debian recently switched from Alioth to Salsa offering only Git hosting from now on and that simplifies the work of exiting contributors and also helps newcomers who are most likely already familiar with Git if they know at least one version control system. (Thanks to everyone involved in the transition!)
Debian recently switched from Alioth to Salsa offering only Git hosting from now on and that simplifies the work of exiting contributors and also helps newcomers who are most likely already familiar with Git if they know at least one version control system. (Thanks to everyone involved in the transition!)
 These are the last hours when we can update packages and they migrate to testing after 10 days right before the full freeze on 5 February.
These are the last hours when we can update packages and they migrate to testing after 10 days right before the full freeze on 5 February. I pledge that before sending each email to the debian-devel mailing list I move forward at least one actionable bug in my packages.
I pledge that before sending each email to the debian-devel mailing list I move forward at least one actionable bug in my packages. I have just finished level one, fixing all RC bugs in
I have just finished level one, fixing all RC bugs in  Hardening all executables by making them position independent by default is basically ready with a few packages to fix (
Hardening all executables by making them position independent by default is basically ready with a few packages to fix (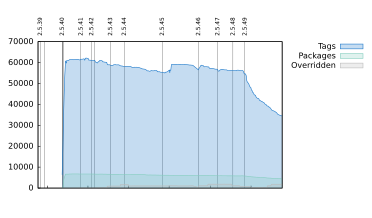
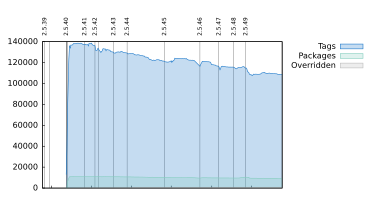
 Shipping Position Independent Executables and using read-only Global Offset Table was already possible for packages but needed package maintainers to opt-in for each package (see
Shipping Position Independent Executables and using read-only Global Offset Table was already possible for packages but needed package maintainers to opt-in for each package (see  With the latest release the Wireshark Project decided to make the Qt GUI the default interface. In line with Debian’s Policy the packages shipped by Debian also switched the default GUI to minimize the difference from upstream. The GTK+ interface which was the previous default is still available from the wireshark-gtk package.
With the latest release the Wireshark Project decided to make the Qt GUI the default interface. In line with Debian’s Policy the packages shipped by Debian also switched the default GUI to minimize the difference from upstream. The GTK+ interface which was the previous default is still available from the wireshark-gtk package. Debian has switched to FFmpeg in testing in July but the work on the package did not stop at that point. After careful testing we can now provide official packages for Jessie users through jessie-backports. See installation instructions
Debian has switched to FFmpeg in testing in July but the work on the package did not stop at that point. After careful testing we can now provide official packages for Jessie users through jessie-backports. See installation instructions